Topic: security
ITOps Times Open-Source Project of the Week: ValidKube
ValidKube combines open-source tools to help ensure Kubernetes YAML best practices, hygiene and security. The tool can verify your Kubernetes configuration files through kubeval, remove clutter from your Kubernetes manifests through kubectl-neat, and can scan YAML code for security vulnerabilities with trivy. RELATED CONTENT: Abstracting complexity from Kubernetes breaks down barrier to entry Kubeval uses … continue reading
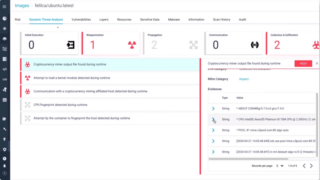
Aqua Security adds new features for assessing security risk
Cloud-native security company Aqua Security is introducing new features that will help companies address their security risk to its Cloud Native Application Protection Platform (CNAPP). According to Aqua Security, users can choose whether to go with a quick assessment of workload risk, or they can actively protect those workloads from attacks in runtime. They can … continue reading
StarlingX R6.0 released by Wind River
StarlingX, the platform that builds out infrastructure from the core to the edge by providing a scalable foundation with OpenStack, has reached its R6.0 release. The platform can be used to build out an organization’s central cloud and can be installed on the edge to manage a smaller pool of resources. In addition, the platform … continue reading
DoControl announces no-code security workflows for SaaS applications
The automated SaaS security company DoControl announced no-code security workflows that brings Zero Trust into the SaaS data layer. DoControl’s security workflows allow for consistent, granular, and customizable data access controls, which helps to close the gaps found in inflexible hard-coded and out-of-the-box policies. “Security teams are becoming increasingly frustrated with the lack of visibility … continue reading
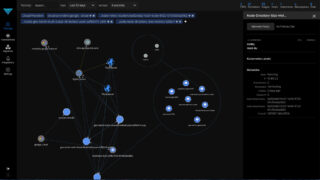
ThreatMapper 1.2.0 released with new attack path visualizations
Observability company Deepfence launched new ThreatMapper features to provide DevSecOps professionals with new attack path visualizations, most exploitable vulnerabilities calculations, and AWS Fargate support. ThreatMapper finds hidden attack paths by continuously correlating vulnerabilities with network traffic, identifying much harder to find vulnerable services that are further downstream, behind proxies and exposed indirectly to potentially malicious … continue reading
ITOps Times Open-Source Project of the Week: NordVPN’s speed test tool
NordVPN developed a new tool that helps users objectively measure and compare the speed of different VPN services. It allows users to add and compare different VPN services, and provides detailed reporting. “Connection speed is one of the most important factors that affect user experience when they use a VPN. People want to secure their … continue reading
ITOps Times Open-Source Project of the Week: Cloud Hypervisor Project
The Linux Foundation announced that it will host the Cloud Hypervisor project, which delivers a Virtual Machine Monitor (VMM) for modern Cloud workloads. The project is supported by Alibaba, ARM, ByteDance, Intel and Microsoft. The project is written in Rust and focuses on security features such as CPU, memory and device hot plug; support for … continue reading
ITOps Times Open-Source Project of the Week: Trivy
Trivy is an open-source project developed by Aqua Security that scans for vulnerabilities and configuration issues in container images, file systems, and Git repositories. It detects vulnerabilities of operating system packages, such as Alpine, RHEL, and CentOS, and language-specific packages, such as Bundler, Composer, npm, yarn, and more. It can also scan Infrastructure as Code … continue reading
Palo Alto Networks launches several new security capabilities
Palo Alto Networks today introduced new products and capabilities including Prisma Cloud 3.0, Cortex eXtended Managed Detection and Response (XMDR) Partner Specialization, and Next-generation CASB. Prisma Cloud 3.0 Prisma Cloud 3.0 is an integrated platform designed to shift security left and to improve a company’s security posture by reducing security risks at runtime. The solution … continue reading
ManageEngine announces new endpoint management capabilities
ManageEngine announced the addition of data loss prevention for endpoints, anti-ransomware and endpoint compliance capabilities to its unified endpoint management (UEM) solution, Desktop Central. This follows a 500% spike in ransomware attacks since the move to remote work last year, according to a Bitdefender report. Also, ManageEngine’s 2021 Digital Readiness Survey found that 83% of … continue reading
Auth0 now available on Microsoft Azure
Auth0 announced that it launched its Auth0 Identity Platform on Microsoft Azure to unlock a secure cloud deployment option for organizations seeking strategic fit with their technology stack. Auth0’s identity platform provides organizations with tools to support security, compliance, and data residency that apply to them. Organizations requiring data residency options can take advantage of … continue reading
Report: Major disconnect between understanding of security importance and implementation
A majority of organizations understand the importance of modern security in cloud native deployments, but few seem to be following through on that. According to a new survey from the Cloud Native Computing Foundation (CNCF), 85% of respondents consider modern security to be of the utmost importance. However, only 9% of those surveyed had a … continue reading