Topic: security
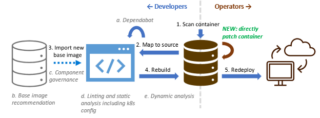
ITOps Times Open-Source Project of the Week: Copa
Copa, short for Copacetic, is an open-source project for vulnerability management. It can automatically apply the necessary patches to a container image based on the results of vulnerability scans. This allows containers to be patched quickly without waiting on a full rebuild upstream, so that they can be redeployed as fast as possible. The maintainers … continue reading
Lacework launches new capabilities for securing cloud environments
The security company Lacework has announced the addition of new capabilities to its platform to help IT and security teams more easily secure their cloud environments. The first new addition is Lacework Explorer, which is designed to provide better visibility into potential threats. It provides a visualization of the relationships between cloud resources, which helps … continue reading
Cloudflare releases two new security solutions for preventing AI-based attacks
Cloudflare has announced two new security solutions designed to help protect against AI-based threats: Defensive AI, a personalized approach to securing organizations against risks caused by AI, and Firewall for AI, which scans LLM prompts for language commonly used in attacks. Defensive AI provides tailored mitigations that enable the protection of critical applications and entire … continue reading
Falco graduates from CNCF
The Cloud Native Computing Foundation (CNCF) announced the graduation of Falco. Falco is a cloud-native security tool for Linux systems and has become a commonly used engine for detecting threats within Kubernetes environments. This milestone marks a significant achievement for Falco, emphasizing its importance and effectiveness in cloud-native security, according to the CNCF. “Real time … continue reading
ManageEngine enhances Log360 with features that improve the accuracy and precision of SIEM
ManageEngine introduced a dual-layered threat detection system in its security information and event management (SIEM) solution, Log360. This feature, part of Log360’s threat detection, investigation, and response (TDIR) component called Vigil IQ, aims to enhance the accuracy and precision of threat detection for security operations center (SOC) teams. The move is in response to challenges … continue reading
Recast Software’s third-party patching catalog now includes over 2,000 applications
The endpoint management solution provider Recast Software has announced the release of its latest software update, version 5.4. This new version, which is now available for download, marks a significant expansion of Recast Software’s third-party patching catalog. The solution now has over 2,000 applications, which provides businesses a comprehensive approach to application management and vulnerability … continue reading
Report: Nearly half of organizations see significant improvement with cyber insurance
A surge in cyber threats has led to a heightened interest in cybersecurity insurance. Nearly half of the organizations surveyed in a recent study conducted by Recast Software and the Ponemon Institute have noticed a significant improvement in their cybersecurity posture after purchasing insurance. However, 48% have switched insurance providers due to various reasons, including … continue reading
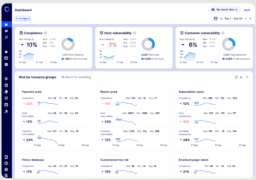
Tufin releases dashboard for tracking security implementation
Tufin announced the launch of Dashboard Essentials, an addition to the Tufin Orchestration Suite. This extension is designed to enhance analytics capabilities for monitoring security, compliance, and operational efficiency. Dashboard Essentials offers customers access to specialized analytics tools, which are crucial for tracking the progress of their security implementations, according to the company. This feature … continue reading
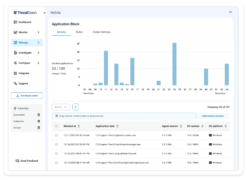
Malwarebytes expands ThreatDown with new feature for blocking unwanted apps from launching
Malwarebytes has announced the introduction of a new feature that stops applications from launching into its endpoint security solution ThreatDown. The new feature, called Application Block, prevents unauthorized, unwanted, or malicious apps from launching. IT teams can specify particular apps that they don’t want opened either, such as apps they deem to hinder productivity. According … continue reading
NIST identifies cyberattacks that manipulate AI behavior
The recent publication by the National Institute of Standards and Technology (NIST) and their partners highlights a significant vulnerability in AI/ML systems: the susceptibility to adversarial attacks. NIST states that the challenge is that training data for AI systems may not always be reliable in a blog post. The data often comes from online sources … continue reading
Cisco to acquire Isovalent
Cisco announced the intent to acquire Isovalent, which provides open-source software and enterprise solutions solving networking, security, and observability needs for modern cloud native infrastructure. Isolavent created Cilium, an eBPF-based networking tool, and contributed it to the CNCF. Through that contribution and collaborations with the community, Isovalent has advanced the project to the status of … continue reading
Qmulos Q-Compliance V4.4.0 and Q-Audit V3.7.0 are generally available
Qmulos has announced the general availability of Q-Compliance V4.4.0 and Q-Audit V3.7.0, two platforms in its suite of compliance, security, and risk management automation solutions. These releases incorporate workflow and ticketing capabilities, empowering organizations to tailor security and compliance investigations, escalations, and approvals according to their unique needs. By providing these customizable processes, Qmulos aims … continue reading