Topic: security
IBM adds enhanced data protection to FlashSystem
IBM announced that it is bringing advanced data protection capabilities to the IBM FlashSystem family of all flash arrays to help companies plan for and recover quickly from ransomware and cyberattacks. IBM Safeguarded Copy, which automatically creates data copies in “immutable snapshots,” will now be integrated into the IBM FlashSystem family. In the event of … continue reading
Report: 94% of organizations have suffered from insider data breaches
A lot of focus is made on hardening systems from outside attacks, but threats from within the company shouldn’t be ignored. Results from Egress’ Insider Data Breach Survey 2021 showed that 94% of organizations have fallen victim to insider data breaches in the last year alone. The survey was conducted by Arlington Research on behalf … continue reading
Cloud Security Alliance releases Enterprise Architecture Reference Guide v2
The Cloud Security Alliance announced the release of the Enterprise Architecture Reference Guide v2, which provides users with a compilation of every domain and container within the CSA Enterprise Architecture v2.3. “This reference guide is fundamentally important for risk managers in evaluating opportunities for improvement, creating road maps for technology adoption, identifying reusable security patterns, … continue reading
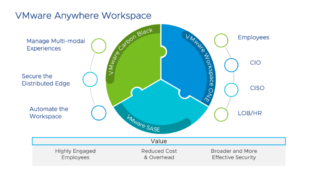
VMware unveils Anywhere Workspace for distributed organizations
VMware wants distributed organizations to be able to embrace work from anywhere with the release of its Anywhere Workspace. The new solution aims to manage multi-modal employee experience while providing better security at the edge and reducing costs and operational overhead. “Organizations are facing many challenges, such as ensuring good connectivity for remote employees, monitoring … continue reading
Report: Fusion of security and network planning is accelerating
The fusion of security and network planning has been accelerating over the past year, according to Aryaka’s recently released 2021 Global State of the WAN report. According to the report, almost a third of companies surveyed are already deploying secure access service edge (SASE) architectures. This close integration of networks and security will become even … continue reading
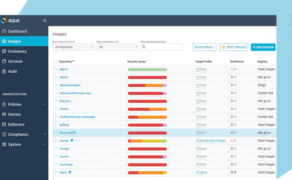
Aqua Security launches Aqua Cloud Native Security Platform for containers and VMs running on Arm devices
Aqua Security launched a new container runtime security solution for Arm 64-bit environments that enables organizations to protect their high-density workloads on platforms such as AWS Graviton2 instances and more. “Our customers will be able to continue and accelerate their cloud native journey with Aqua’s support for Arm-based architectures. Through our commitment to supporting the … continue reading
ITOps Times Open-Source Project of the Week: pfSense
This week’s featured project of the week is pfSense, a free network firewall distribution. It is based on the FreeBSD operating system, includes a custom kernel and provides the same or more functionality of common commercial firewalls with no artificial limitations. It is currently used around the world from companies like Check Point, Cisco PIX, … continue reading
Rapid7 acquires Kubernetes security provider Alcide
Rapid7 acquired the Kubernetes provider Alcide to help its customers rapidly adopt and secure cloud environments. Alcide provides Kubernetes security fully integrated into the DevOps lifecycle and processes so that business applications can be rapidly deployed while also protecting cloud environments from malicious attacks, according to Brian Johnson, the SVP of Cloud Security Practice at … continue reading
Red Hat to acquire Kubernetes and container security company StackRox
Red Hat has entered into an agreement to acquire StackRox for its container and Kubernetes-native security capabilities. According to Red Hat, bringing StackRox to its container application platform OpenShift will help users build, deploy and securely run apps across the hybrid cloud from a single platform. In addition, Red Hat plans to use StackRox to … continue reading