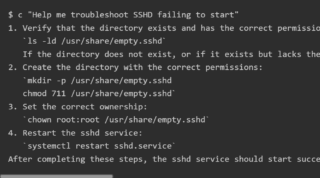
Cloudflare now blocks AI crawlers by default, introduces pay per crawl model
Last year, Cloudflare introduced a setting that allowed website owners to block AI crawlers. Today, the company is announcing that this setting will now be the default rather than a user needing to switch it on. The company explained that by switching to a permission-based model, it is eliminating the need for content owners to …
AI updates in ITOps platforms announced in June
Mirantis launches its AI Factory Reference Architecture The AI Factory Reference Architecture provides blueprints for building and managing AI factories. Utilizing the company’s k0rdent AI platform that provides a templated, declarative model for rapid provisioning, the AI Factory Reference Architecture will enable AI workloads to be deployed within days of hardware being installed. According to …
Komodor adds new cost optimizing capabilities to its Kubernetes management platform
Komodor is adding new cost optimization capabilities across its Kubernetes management platform so that organizations can reduce costs while still maintaining reliability across their Kubernetes environment. According to Komodor, IT teams often overspend on compute because right-sizing workloads can be difficult as a result of lack of expertise, the large volume of factors to consider, …
Pure Storage introduces Enterprise Data Cloud to enable centralized management of data and storage across on-premises, public cloud, and hybrid environments
Pure Storage is introducing a simpler approach to data and storage management that it says will allow organizations to focus more on business outcomes than on infrastructure. Enterprise Data Cloud (EDC) allows IT teams to centrally manage a virtualized cloud of data regardless of how many different locations it’s stored in, spanning on-premises, public cloud, …
Latest News
VMware Cloud Foundation 9.0 delivers a “modern private cloud”
Broadcom has announced the release of VMware Cloud Foundation (VCF) 9.0, an update that it promises will provide “the agility and scalability of public cloud with the security, performance, architectural control and total cost of ownership (TCO) benefits of an on-premises environment.” It introduces a new unified interface for cloud administrators, including a new Quick …
Enterprise AI: A new game plan for storage IT professionals
As artificial intelligence (AI) becomes deeply embedded in enterprise operations, IT storage professionals are being pulled into uncharted territory. Where once their focus was confined to provisioning, performance tuning, data protection and backups, today they are expected to orchestrate data services, ensure regulatory compliance, optimize cost models, and even help train AI models. The transition …
Mirantis AI Factory Reference Architecture provides templates to support deployment and management of AI infrastructure at scale
Mirantis is introducing its AI Factory Reference Architecture, which provides blueprints for building and managing AI factories. Utilizing the company’s k0rdent AI platform that provides a templated, declarative model for rapid provisioning, the AI Factory Reference Architecture will enable AI workloads to be deployed within days of hardware being installed. According to Mirantis, cloud-native workloads …
Crack the Code: How Network Observability Unlocks Revenue Growth for Service Providers
Today’s service providers are operating in an era of relentless digital evolution, a time when standing still means falling behind. As they navigate a brutal battleground of cutthroat competition and sky-high customer demands, continued innovation is a must. To ensure their growth and very survival, managed service providers (MSPs), communication service providers (CSPs), and telecommunication …
Cisco prepares for AI-ready data centers with new innovations, partnerships
During its annual conference, Cisco Live, Cisco announced several new offerings and partnerships that support its transition from traditional to AI-ready data centers. “Cisco is at the forefront of enabling organizations to harness the power of AI with solutions that are scalable, efficient, and, above all, secure. Our evolving portfolio lays the groundwork for AI-ready …
Contrast Security’s Northstar unifies app security for developers, security, and operations
Contrast Security has announced the launch of Northstar, a security platform update that brings developers, security, and operations teams together to address app security in a more unified way. “We’re calling this release Northstar because it points the way forward. It helps customers see what was once invisible — adding clarity where there was ambiguity, …
Opsera, Databricks expand partnership with DevOps for DataOps, Cloudera joins AI-RAN Alliance, and more: ITOps News Digest
AI-powered DevOps platform provider Opsera today announced the expansion of its Databricks partnership with the launch of its DevOps for DataOps capability, a Built on Databricks solution. Customers of Opsera and Databricks can use the solution to orchestrate end-to-end analytics and streamline delivery pipelines, the company wrote in its announcement. This is done through the …
Hope for Spring, Prepare for Frost: How to Think About AI’s Next Phase
Are we heading for another big freeze? ‘AI winter’ is a term that first emerged in the late 1970s, as disillusionment with contemporary AI projects came to a peak. Expectations were built up throughout previous decades with scientists and researchers expressing their intention to create machines that could think like humans. But eventually, the public …
AI updates in ITOps platforms announced in May 2025
IT vendors are constantly trying to add more and more AI features to their platforms to help IT operations teams be more efficient and productive. Here are several of those updates from the past month. Red Hat Summit news: RHEL 10, OpenShift Lightspeed Red Hat made several announcements at its Summit event, including the announcements …
Cisco Duo IAM launches to address identity threats
Cisco has announced a new security offering to combat identity threats, which the company says are increasing in frequency as a result of AI. The company’s 2025 Cybersecurity Readiness Index found that almost a third of companies rank identity as their top cybersecurity challenge. “The security industry is facing an ‘identity crisis’ as persistent identity-based …
data
Learning Center
-
Webinars
NetOps with Broadcom – Microwebinar Series
In this microwebinar series with Broadcom, Jeremy Rossbach, Chief Technical Evangelist for NetOps, provides essential insights and actionable strategies for network operations and explores practical strategies to enhance network resilience and accountability, achieve advanced visibility across hybrid environments, and transition from basic monitoring to comprehensive network observability for optimized performance. …
-
Webinars
AI’s Impact on Network Engineering and Operations – Microwebinar Series
AI’s Impact on Network Engineering and Operations Join Phil Gervasi from Kentik for this insightful 15-minute microwebinar where we will dive straight into the essential aspects of AI and uncover the practical realities of its application in network engineering, netops, and network architecture. …
-
White Papers
AI meets Network: Now what?
There’s a lot of buzz about AI in networking, but it can’t be real…right? Join our webinar where we’ll explore both the potential and the limitations of AI, providing a balanced view on its practical applications. By the end of this webinar, you’ll have a clear understanding of where AI can genuinely add value and …
-
Webinars
4 Requirements for a Single Pane of Glass in IT Operations
AVAILABLE NOW | For years, technology vendors have promoted the ‘single pane of glass’ as a silver bullet for service-oriented management. The promise was simple: buy this mega-suite of tools and get a single view of your IT environment. Unfortunately, the promise of a single pane of glass for IT operations and management has resulted …
-
Webinars
ITOps Times Live! Microwebinar Series – Internet Resilience
WATCH THE FULL SERIES Every business today relies on the Internet for critical business operations, and IT professionals must ensure Internet Resilience for their company’s customers and workforce. But what does that mean and how can they monitor everything in the digital delivery chain when so much is out of their control? The answer: Internet Performance …
-
Webinars
The State of AIOps 2023: Delivering Value but Falling Short of Expectations
AVAILABLE NOW | Hype continues to build around artificial intelligence and its implications for business and our everyday lives. But seven years after Gartner coined the term AIOps–artificial intelligence for IT operations–just what is the state of AIOps development and adoption in the enterprise IT world? To find out, OpsRamp commissioned a survey of enterprise …
ITOps Times Newswire
- Kentik Launches Cause Analysis to Bring Network Expertise to Every Infrastructure Engineer
- Commvault Extends Support to Red Hat OpenShift Virtualization Workloads for Enhanced, Cloud-Native Cyber Resilience
- Causely’s New Integration with Grafana Labs Goes Beyond Observability to Understandability
- Opsera and Lineaje Partner to Deliver Agentic AI-Powered Security at Scale
- ServiceNow to Extend Leading Agentic AI to Every Employee for Every Corner of the Business With Acquisition of Moveworks
- Causely Launches New Integration with OpenTelemetry
- Xurrent Acquires Zenduty, Completing the Incident Response and Remediation Loop
- Edera Raises $15 Million Series A to Transform Cloud and AI Infrastructure Security
- Cloudflare Launches One-Click Content Credentials to Track Image Authenticity and Preserve Creator Attribution
- Palo Alto Networks Prepares Organizations for Quantum Security with QRNG Open API
- LogicMonitor and OpenAI Supercharge Data Center Operations
- Linux Foundation launches Supporters for Chromium-based browsers