Topic: security
Applying agentic AI to legacy systems? Prepare for these 4 challenges
Agentic AI has enormous potential to add efficiency and speed to legacy system transformation. However, given the complexity of legacy platforms and their critical role in enabling business processes, fully leveraging AI agents to assist with legacy system migration and modernization can be a deeply challenging task. Fortunately, these issues are solvable. They do, however, … continue reading
KnowBe4 shares five key strategies to follow to avoid phishing scams in the enterprise
KnowBe4, a security training platform, is sharing five strategies organizations should take to avoid phishing scams. According to recent research from the company, between November 2024 and February 2025 there was a 57.7% increase in successful phishing attacks. Since phishing attacks target humans, it’s important to properly train employees to avoid them. Here are five … continue reading
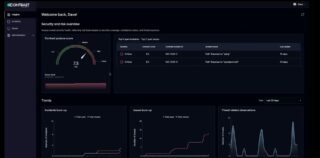
Contrast Security’s Northstar unifies app security for developers, security, and operations
Contrast Security has announced the launch of Northstar, a security platform update that brings developers, security, and operations teams together to address app security in a more unified way. “We’re calling this release Northstar because it points the way forward. It helps customers see what was once invisible — adding clarity where there was ambiguity, … continue reading
Cisco Duo IAM launches to address identity threats
Cisco has announced a new security offering to combat identity threats, which the company says are increasing in frequency as a result of AI. The company’s 2025 Cybersecurity Readiness Index found that almost a third of companies rank identity as their top cybersecurity challenge. “The security industry is facing an ‘identity crisis’ as persistent identity-based … continue reading
DefectDojo unifies SOC and AppSec capabilities in latest platform update
DefectDojo has announced the release of new Security Operations Center (SOC) capabilities in DefectDojo Pro. According to the company, with this update, the platform now acts as a unified platform for both SOC and AppSec teams. It brings together SOC alerts and AppSec findings and has features that aim to cut down on alert noise … continue reading
Linux Foundation and OpenSSF launch Cybersecurity Skills Framework
The Linux Foundation and Open Source Security Foundation (OpenSSF) have announced the Cybersecurity Skills Framework, designed to help organizations identify their security competencies across several areas that are important to reducing cybersecurity risk. “This framework is a valuable tool for CIOs, CISOs, and enterprise learning teams,” said Clyde Seepersad, SVP and general manager of Linux Foundation … continue reading
ManageEngine’s PAM360 now offers AI generated least privilege policies
ManageEngine has added a number of AI-based capabilities to its privileged access management platform PAM360. According to the company, traditional PAM models rely on static policies and don’t have sufficient context, resulting in excessive permissions, entitlement drift, and configuration errors. These updates aim to reduce those issues by automating the process of generating least privilege … continue reading
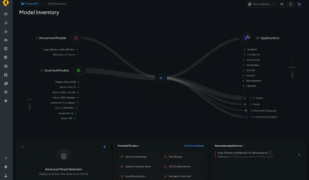
Palo Alto Networks secures AI ecosystem with launch of Prisma AIRS
Palo Alto Networks has announced the availability of Prisma AIRS, a new AI security platform designed to protect an organization’s entire AI ecosystem, including AI apps, agents, model, and data. It ensures safe adoption of AI by scanning models for vulnerabilities, assessing risks associated with the AI ecosystem (ex. sensitive data exposure or platform misconfigurations), … continue reading
RSAC 2025: Bugcrowd to offer red-team-as-a-service, Netwrix expands 1Secure platform, and more
RSA Conference is taking place this week in San Francisco, and the first day kicked off with a number of announcements from security companies. Here are some highlights from the event. Bugcrowd announces “Red-team-as-a-service” offering The new offering will connect customers with a network of vetted ethical hackers that can take on red teaming tasks. … continue reading
Qualys Policy Audit automates compliance and risk management for security teams
Qualys, a company that provides IT compliance solutions, has announced the launch of Policy Audit, a new offering that automates audit preparation and ensures that organizations are ready for an audit any time. According to Qualys, auditing, reporting, and system remediation are time consuming, manual tasks that can be prone to human error. By introducing … continue reading
1Password adds new capability to enable AI agents to securely access and manage secrets
1Password announced new and upcoming updates to its Extended Access Management platform. Announced last year, Extended Access Management promises to “secure every sign-in, for every app, on every device.” Available today, the company announced a new SDK for Agentic AI within the platform to allow developers to enable the AI agents they build to securely … continue reading
Capital One Databolt tokenizes data to reduce risks associated with data breaches
Capital One is introducing a new solution that provides a way to protect sensitive data to reduce the risk of data being exposed during a breach. Capital One Databolt is a tokenization solution that replaces sensitive data with secure tokens. It preserves the underlying data format, which allows companies to still run their applications, manage … continue reading