Topic: containers
Edera releases open source container security benchmark and runtime scanner
Edera, provider of a secure-by-design Kubernetes and AI solution, today announced the availability of Am I Isolated, an open-source container security benchmark that probes users runtime environments and tests for container isolation. The Rust-based container runtime scanner runs as a container and detects gaps in users’ container runtime isolation. It also provides guidance to improve … continue reading
Octopus Deploy releases features to simplify Kubernetes continuous delivery
Octopus Deploy has recently launched new features to help simplify Kubernetes continuous delivery at scale. “Kubernetes is powerful but gets complicated when deploying hundreds or thousands of applications,” Colin Bowern, SVP of Product at Octopus Deploy, said in the company’s announcement. “Challenges like managing environments, lack of pipeline visibility, and compliance get more complex at … continue reading
Red Hat Enterprise Linux 9.3 released, RHEL 8.9 out in a few weeks
Red Hat has announced the release of Red Hat Enterprise Linux (RHEL) 9.3, with Red Hat Enterprise Linux 8.9 coming in the next few weeks. These releases include updates designed to support containers, including an expansion of the Podman integration already present in RHEL. Podman is a tool for deploying, running, building, and sharing Linux … continue reading
ITOps Times Open-Source Project of the Week: Cilium
Cilium provides eBPF-based networking, observability, and security for container workloads. It enables users to secure network connectivity between application services deployed using Linux container management platforms like Kubernetes. Cilium is built upon a Linux kernel technology known as eBPF. This technology allows for the real-time integration of robust security, visibility, and network control logic directly … continue reading
Mend for Containers offers container scanning at scale
The application security company Mend.io is working to make containers more secure with the release of Mend for Containers, which scans container images and registries. According to the company, the new solution will enable DevSecOps teams to discover threats before they make it to production. It also can scan containers that are already in production. … continue reading
How to think about managing modern application workloads
Workloads are the workhorses of your mission-critical applications—they’re what get the job done. The environments that these workloads run in, and the way we manage them, have evolved significantly. Back in the old days, applications were built as monoliths. They were self-contained systems that included not just the capabilities you needed them for but also … continue reading
CNCF Annual Survey reveals containers have become standard practice
44% of organizations stated that they are already using containers for almost all of their applications and business segments while another 35% reported that containers are used for at least a few production applications. This is according to the CNCF Annual Survey 2022, conducted by the Cloud Native Computing Foundation (CNCF) and Linux Research Foundation. … continue reading
Cloud Native Guide
The cloud native guide is a listing of cloud-native security tool providers, along with a brief description of their offerings. … continue reading
ITOps Times Open-Source Project of the Week: Otomi
Otomi is intended to act as an extension of Kubernetes to turn it into a “full blown container platform.” It provides an advanced ingress architecture, a suite of integrated pre-configured applications, multi-tenancy, and governance and security policies. One of the goals of the project is to support common DevOps use cases. It strongly relies on … continue reading
Cloud Security Alliance releases Enterprise Architecture Reference Guide v2
The Cloud Security Alliance announced the release of the Enterprise Architecture Reference Guide v2, which provides users with a compilation of every domain and container within the CSA Enterprise Architecture v2.3. “This reference guide is fundamentally important for risk managers in evaluating opportunities for improvement, creating road maps for technology adoption, identifying reusable security patterns, … continue reading
ITOps Times Open-Source Project of the Week: Longhorn
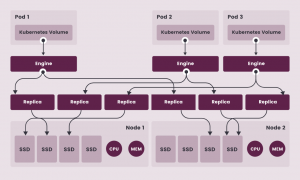
Longhorn is an open-source distributed block storage system for Kubernetes. It is built using Kubernetes and container primitives, making it cloud-native storage, according to the team. “Longhorn implements distributed block storage using containers and microservices. Longhorn creates a dedicated storage controller for each block device volume and synchronously replicates the volume across multiple replicas stored … continue reading
Report: Releasing microservices into production a challenge for many organizations
Despite having become mainstream over the past few years, many organizations still struggle with actually releasing microservices into production. According to the State of Cloud-Native Release Orchestration 2021 report from Vamp, 72% of respondents use Kubernetes and 81% use microservices in production, but nearly 9 in 10 respondents report challenges and issues when releasing microservices … continue reading