Topic: cybersecurity
Report: Nearly half of organizations see significant improvement with cyber insurance
A surge in cyber threats has led to a heightened interest in cybersecurity insurance. Nearly half of the organizations surveyed in a recent study conducted by Recast Software and the Ponemon Institute have noticed a significant improvement in their cybersecurity posture after purchasing insurance. However, 48% have switched insurance providers due to various reasons, including … continue reading
ITOps Open-Source Project of the Week: Spiderfoot
SpiderFoot is an open-source tool designed to automate OSINT (Open Source Intelligence) for threat intelligence and mapping attack surfaces. The project enables the exploration of a target using a wide range of data sources, thus aiding in cybersecurity, infosec, and threat intelligence. SpiderFoot can be used for various purposes, including reconnaissance, information gathering, and security … continue reading
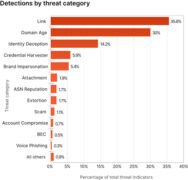
Report: Phishing is most dominant cyber attack
Phishing remains the most dominant and fastest-growing Internet crime, largely due to the ubiquity of email and the ceaseless issue of human error that is preyed upon by today’s threat actors, according to Cloudflare’s inaugural 2023 Phishing Threat Report. The impact of phishing is not limited to large corporations; it affects small businesses, local entities, … continue reading
Bitdefender GravityZone Security for Mobile offers improved mobile threat detection to enterprises
Cybersecurity company Bitdefender today announced GravityZone Security for Mobile. This release is intended to offer companies enhanced mobile threat detection (MTD) and security for Android, iOS, and Chromebook devices. It delivers deeper visibility into the mobile footprint of enterprises, managed service providers, and their users so they can better prevent, locate, and respond to cyberattacks … continue reading
CrowdStrike announces Charlotte AI for faster threat reaction
CrowdStrike announced a new generative AI cybersecurity analyst called Charlotte AI. The AI will help to reduce the cybersecurity skills gap and enable faster reactions to threats posed by adversaries. It is currently available only in private customer preview. Charlotte AI uses advanced security data and a structured feedback system to give customers answers to … continue reading
Cloudflare announces zero-trust solution for companies experimenting with AI
Cloudflare One for AI was released as a collection of features that help teams build with the latest AI services while maintaining a zero-trust security posture. “Cloudflare One’s goal is to allow you to safely use the tools you need, wherever they live, without compromising performance. These features will feel familiar to any existing use … continue reading
Google announced a new training program to expand the cybersecurity workforce
Google announced a new training program built by cybersecurity experts that aims to expand the cybersecurity workforce by filling major skills gaps in the United States and providing opportunities for people from a wide range of backgrounds. The new Google Cybersecurity Certificate provides job seekers with affordable paths to careers in data analytics, IT support, … continue reading
Report: Millions in lost revenue caused by Internet disruptions
A new Catchpoint survey in collaboration with Forrester Consulting found that nearly 40% of all respondents suffer customer-impacting disruptions, which cost up to $1 million per month. For most of those companies – mostly consumer brands and retailers with a significant volume of online transactions and a company size of over 1,000 employees – even … continue reading
Dell strengthens security with new services and solutions portfolio
Dell launched new services and solutions to strengthen their security portfolio and to protect its customers from cyber threats and malicious attacks. The company released its Dell Technologies Managed Detection and Response Pro Plus fully managed security operations solution with capabilities that block routes to cyber-attacks and accelerate the recovery process if an attack occurs. … continue reading
SentinelOne adds new integrations to Singularity Marketplace
The autonomous cybersecurity platform SentinelOne announced integrations with Revelstoke, Fletch, Code42, and KnowBe4 to offer new use cases in the Singularity Marketplace. Organizations can optimize their security workflows by integrating SentinelOne Singularity Platform with Revelstoke‘s Security Orchestration, Automation, and Response (SOAR) capabilities, allowing for the automation of alert triage and incident remediation. SentinelOne alert triage … continue reading
Lumos launches App Governance Platform to cut IT spending while maintaining security
The newly launched Lumos App Governance Platform automates access requests, enforces least privilege, speeds up user access reviews, and eliminates extra SaaS app spending. Lumos is dedicated to bridging the gap between IT, security, compliance, and finance by providing support for the most important functions for businesses in this economic climate, namely, cost management and … continue reading
Tenable announces new exposure management platform
Tenable today announced the release of Tenable One, an Exposure Management Platform to unify discovery and visibility into all assets to assess their exposures and vulnerabilities across an entire attack surface. The platform brings the organization’s entire attack surface (both on-premises and cloud-based) into a single view. It aggregates vulnerability data across the IT infrastructure, … continue reading