Topic: cybersecurity
Report: Emerging threats are the biggest weakness for enterprise security
Technology advancement is giving organizations and individuals the ability to innovate faster, but it is also enabling hackers to evolve their efforts as well. According to a recent report, 45% of enterprises believe emerging threats are one of the biggest issues when it comes to their security infrastructure, followed by staffing and limited resources. The 6-12 … continue reading
How will augmented reality drive change in cybersecurity?
Augmented reality is a powerful technology with far-reaching implications. That said, there’s one sector in which it hasn’t yet reached its full potential: Cybersecurity. AR technology could bring about some incredibly positive changes, up to and including solving the talent shortage. I’d like you to imagine the following scenario. An automated intrusion detection system flags … continue reading
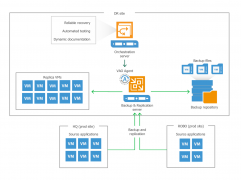
ITOps Times news digest: Veeam Availability Orchestrator v2, Citrix Workspace on Google Cloud, and Tenable’s Cyber Exposure ecosystem
Veeam Software has announced that it is expanding its orchestration capabilities in the latest release of the Veeam Availability Orchestrator. Version 2 will allow organizations to address a wider range of disaster recovery and data migration use cases. Specific new features include the ability to more easily prove SLA attainment; leverage backup and replica data; … continue reading
IT operations monitoring can help prevent business services failures
As IT organizations move towards digitizing services and operations, there is an ever-increasing dependence on the IT infrastructure that supports these needs. It follows that any degradation of performance of the infrastructure directly affects the manner in which business is conducted and, therefore, the bottom line. A quick Google search reveals several recent examples. And … continue reading
Malwarebytes: Mid-sized companies suffer the most in cybersecurity attacks
Cybercrime incidents continue to rise, and the cost of remediation for those incidents is also rising. A newly released report found organizations with about 2,500 employees in the US spend almost $1.9 million per year on cyber-security related costs. The survey is based off of 900 security professionals, sponsored by Malwarebytes and conducted by Osterman … continue reading
When your trusted employees leave, so will your IP
The American economy is strong and the unemployment rate is at a 17-year low. Depending on which study you believe, either 40 percent or 70 percent of U.S. working people are looking to make a job move soon. These statistics make security practitioners nervous — let’s be honest we are always nervous. The reason these … continue reading
Corero: The Memcached vulnerability is worse than originally thought
Corero Network Security has disclosed that the Memcached vulnerability that was responsible for last week’s GitHub DDoS attack is more extensive than originally reported. It is now known that the vulnerability can be used to steal or modify data from the Memcached servers. Memcached is an open-source system that stores data in memory to speed … continue reading
A 5-step protection plan against ransomware
Ransomware has cost US businesses over $75 billion. According to the FBI, there are over 4,000 attacks every single day. If your organization hasn’t experienced an attack, it will. In a recent webinar sponsored by Veriato RansomSafe, Nick Cavalancia, founder of Techvangelism laid out a five step plan to thwart ransomware attacks that businesses can … continue reading
Check Point Software announces CloudGuard: Complete gen V cyber protection for the cloud
Check Point Software Technologies Ltd., a leading provider of cyber-security solutions globally, has today announced the CloudGuard product family to protect enterprises from Gen V cyber attacks on cloud applications and infrastructure. Check Point is also introducing CloudGuard SaaS protecting enterprises against cyber attacks on SaaS applications. CloudGuard is a part of the Check Point Infinity architecture, built … continue reading
Risks of SAP: How to protect your company from a cyberattack
If you work for a company that uses an enterprise resource planning (ERP) system, then odds are you’re familiar with SAP. SAP is the ERP of choice for a majority of businesses worldwide. And for good reason: it deftly handles everything from supply chain management to human resources to finance and beyond. If you need … continue reading
Check Point prepares for next-gen cybersecurity attacks with Infinity Total Protection
Check Point announced a new security consumption model designed to prevent Gen V cyberattacks at the cybersecurity summit CPX 360 in Barcelona this week. The Check Point Infinity Total Protection solution is designed to provide real-time protection against advanced mobile, cloud and enterprise network attacks. “Cyberattacks are getting bigger, more sophisticated and more complex daily, … continue reading