Topic: devsecops
Sumo Logic adds threat intelligence to its log analytics platform
Sumo Logic has announced new AI and security analytics capabilities designed to allow security and development teams to use critical security data to plug security holes. The Sumo Logic Saas Log Analytics Platform now provides a single place to monitor and secure applications and infrastructure so all stakeholders using DevSecOps practices can work together to … continue reading
Code execution vulnerabilities: Three preventative steps you need to take now
Hidden software vulnerabilities are silent nightmares waiting to awaken chaos. Though security is still a priority with the rise of DevSecOps, there continues to be a sharp increase in exploitable vulnerabilities this year compared to last. Among these vulnerabilities, code execution attacks stand out as some of the sneakiest and worst threats. Remote code execution … continue reading
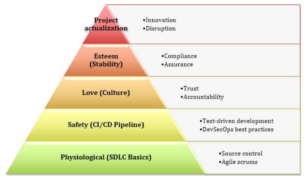
Maslow’s Hierarchy of DevSecOps
When psychologist Abraham Maslow came up with his hierarchy of needs pyramid in the 1940s, he probably didn’t know what a behemoth he was creating. Those five simple stages were a baseline that applied to so much more than individuals. That’s especially true when we think about software and the human-centric processes we use in … continue reading
Aqua Security and D2iQ partner on securing cloud-native apps
D2iQ announced a partnership with Aqua Security that will enable organizations to create seamless DevSecOps experiences that accelerate the deployment of secure smart cloud-native applications. With the partnership, organizations can run Aqua’s Cloud Native Application Protection Platform (CNAPP) on the D2iQ Kubernetes Platform (DKP) and enhance the security of containerized workloads. Aqua on DKP can … continue reading
JFrog announces JFrog Connect for managing IoT devices
JFrog today announced Connect, a solution designed to help developers update, manage, monitor, and secure remote Linux and IoT devices at scale that is a fully integrated part of the JFrog Platform. Organizations can fully automate DevSecOps activities across hundreds of thousands of devices using a consistent operational model and intuitive user interface across cloud, … continue reading
Weave GitOps 2022.03 released with new policy as code updates
The GitOps company, Weaveworks, has announced the release of Weave GitOps 2022.03. This comes as an update to the full-stack GitOps platform to automate application delivery and secure infrastructure operations on premise, in the cloud, or at the edge. Teams can now securely deploy and manage applications continuously with built in policy as code within … continue reading
ThreatMapper 1.2.0 released with new attack path visualizations
Observability company Deepfence launched new ThreatMapper features to provide DevSecOps professionals with new attack path visualizations, most exploitable vulnerabilities calculations, and AWS Fargate support. ThreatMapper finds hidden attack paths by continuously correlating vulnerabilities with network traffic, identifying much harder to find vulnerable services that are further downstream, behind proxies and exposed indirectly to potentially malicious … continue reading
PagerDuty brings security closer to operations
PagerDuty wants to unify the security operations among developers, operations and security teams. The company announced PagerDuty for Security Operations with new and existing security integrations across the company’s ecosystem. “With PagerDuty for Security Operations, we now bring security professionals into the fold to operate in a unified platform to engage in real-time security response,” … continue reading
Cloud security company Threat Stack acquires Bluefyre for its targeted application security
Cloud security and compliance company Threat Stack wants to bolster its cloud capabilities with the acquisition of Bluefyre. According to the company, Bluefyre will help deliver greater visibility into security as well as help developers build secure, cloud-native apps. Bluefyre provides targeted application security for Kubernetes, Mesosphere and OpenShift applications, and according to Threat Stack … continue reading
Security and compliance in DevSecOps
In the space of time it takes you to read this blog post and finish your morning coffee, a company at the vanguard of DevSecOps, such as Etsy, Amazon or Netflix, will have completed yet another deployment – one of potentially thousands per day. Deployment frequency has accelerated to a pace that would have been … continue reading
Chef InSpec 3.0 released with compliance audits and remediation capabilities for DevSecOps
Chef has announced a major release to its compliance automation platform InSpec. Version 3.0 of the solution includes a new plugin architecture, improved usability, enhanced management and automation compliance for Terraform, and improved performance. According to the company, this release is meant to target DevSecOps teams. In addition, the release includes a number of bug … continue reading