Topic: security
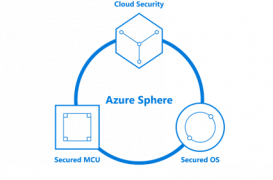
Microsoft introduces Azure Sphere for secure, Internet-connected microcontroller powered devices
Microsoft announced the preview of Microsoft Azure Sphere at the RSA 2018 security conference this week in San Francisco this week. Microsoft Azure Sphere is a new tool designed for creating secure, Internet-connected microcontroller (MCU) powered devices. According to the company, a MCU is a tiny chip that acts as the brain of intelligent devices … continue reading
Twistlock 2.4 released with advanced cloud native security
Twistlock has announced the availability of Twistlock 2.4. This is the 13th major release of its container security solution for Docker, Kubernetes and other cloud-native tools. The new release comes with expanded protection for all environments, including those still running on VMs. “As container adoption grows, our customers are both scaling their deployments and sharing them … continue reading
NeuVector 2.0 automates Kubernetes security incident detection and response
NeuVector, the leader in Kubernetes security delivering the first and only multi-vector container firewall, today announced NeuVector 2.0. The enhanced security solution further protects Kubernetes environments by building on the unique NeuVector run-time security automation, which combines east-west traffic visibility with container process monitoring and vulnerability scanning. NeuVector 2.0 adds important new capabilities that include a Kubernetes … continue reading
HashiCorp Vault 0.10 released with more authentication options
Cloud infrastructure automation provider HashiCorp is strengthening identity-based cloud security with the latest release of HashiCorp Vault. Vault is the company’s tool for securing, storing, and controlling access to tokens, passwords, certificates, API keys and other secrets. The latest release, version 0.10, features the ability to leverage any trusted source of identity to enforce access … continue reading
Code42 introduces Forensic File Search to enhance security
Code42 today introduced a new product to deliver near real-time answers to complicated data security questions. Code42 Forensic File Search intends to assist security, IT, and compliance professionals in reducing the amount of time it takes to investigate, respond to, and recover from data security incidents. “Code42 Forensic File Search is a game-changer for security … continue reading
Container security pioneer StackRox secures $25 Million in series B funding
StackRox, the leader in security for containerized cloud-native applications, announced today that it has secured $25 million in Series B funding. This funding round is being led by Redpoint Ventures and includes follow-on investments from Sequoia Capital and Amplify Partners. StackRox delivers the industry’s only solution that offers continuous detection for applications running on container technologies, including Docker and Kubernetes. … continue reading
Setting up an SSH CA
When I first started looking after Unix systems, I spent most of my days in a remote shell. If you didn’t live in the data centre, that’s what you did, even before ssh replaced telnet. Since moving to Kubernetes, logging into a server may have become less common, but when things go really wrong, I … continue reading
Corero: The Memcached vulnerability is worse than originally thought
Corero Network Security has disclosed that the Memcached vulnerability that was responsible for last week’s GitHub DDoS attack is more extensive than originally reported. It is now known that the vulnerability can be used to steal or modify data from the Memcached servers. Memcached is an open-source system that stores data in memory to speed … continue reading
A 5-step protection plan against ransomware
Ransomware has cost US businesses over $75 billion. According to the FBI, there are over 4,000 attacks every single day. If your organization hasn’t experienced an attack, it will. In a recent webinar sponsored by Veriato RansomSafe, Nick Cavalancia, founder of Techvangelism laid out a five step plan to thwart ransomware attacks that businesses can … continue reading
NAKIVO expands disaster recovery functionality Backup and Replication v7.4
Virtualization and cloud backup company NAKIVO has announced version 7.4 of NAKIVO Backup and Replication with a long list of features and improvements. According to the company, the biggest feature of the release is the automated VM disaster recovery for VMware, Hyper-V and Amazon Web Services. “The new version [of Backup and Replication] provides … continue reading
Data security still main reason for staying out of cloud, study finds
According to LogicMonitor’s “The Future of the Cloud – Cloud Influencers Survey,” by 2020, the share of workloads running in the public cloud could increase by 10 percent, from 31 to 41 percent. Despite this growth, some holdouts remain that prefer their self-managed on-site databases, citing concerns over the security of off-site managed database solutions, … continue reading
Check Point Software announces CloudGuard: Complete gen V cyber protection for the cloud
Check Point Software Technologies Ltd., a leading provider of cyber-security solutions globally, has today announced the CloudGuard product family to protect enterprises from Gen V cyber attacks on cloud applications and infrastructure. Check Point is also introducing CloudGuard SaaS protecting enterprises against cyber attacks on SaaS applications. CloudGuard is a part of the Check Point Infinity architecture, built … continue reading