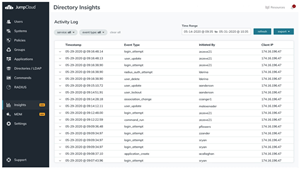
JumpCloud announced Directory Insights, its new event logging feature that provides IT administrators with a complete picture of an end user’s access and access rights.
“It’s a challenge to track all the changes that can happen to a user’s access, all of the applications they access, and furthermore when things go wrong, pinpoint the root cause of an issue,” JumpCloud wrote in a post. “Directory Insights gives administrators a central place to audit activity across all of JumpCloud’s core services.”
Directory Insights logs events on admin changes in the directory; logins to the User/Admin Portal; user authentications to SAML applications and via RADIUS; logins to macOS, Windows, and Linux systems; and authentications via LDAP.
Additionally, IT administrators can track which applications users access, see if MFA is used, and identify failed login attempts. Admins can query a list of all users created within a time frame using a curl request to JumpCloud’s API endpoint.
In order to filter and search through data, admins only need an API key and a JSON POST body to the “start_time”, the date in which they would like to start their query.
In the JSON response, JumpCloud captures metadata about the event to provide a complete picture on what occurred. It then provides information such as who initiated the event, when did it happen, the user agent information about the browser and system used, client ip and geoip data on the location of an event, and the exact details on what was changed, the company explained.
“The power of Directory Insights comes when you string together a series of events to provide a complete picture of every change to a user and all of the resources they authenticate to,” JumpCloud wrote.
Directory Insights is available as a premium add-on to JumpCloud’s Directory-as-a-Service, which is used for managing identities and systems in the cloud.








