KnowBe4 shares five key strategies to follow to avoid phishing scams in the enterprise
KnowBe4, a security training platform, is sharing five strategies organizations should take to avoid phishing scams. According to recent research from the company, between November 2024 and February 2025 there was a 57.7% increase in successful phishing attacks. Since phishing attacks target humans, it’s important to properly train employees to avoid them. Here are five … continue reading
Cloudflare now blocks AI crawlers by default, introduces pay per crawl model
Last year, Cloudflare introduced a setting that allowed website owners to block AI crawlers. Today, the company is announcing that this setting will now be the default rather than a user needing to switch it on. The company explained that by switching to a permission-based model, it is eliminating the need for content owners to … continue reading
AI updates in ITOps platforms announced in June
Mirantis launches its AI Factory Reference Architecture The AI Factory Reference Architecture provides blueprints for building and managing AI factories. Utilizing the company’s k0rdent AI platform that provides a templated, declarative model for rapid provisioning, the AI Factory Reference Architecture will enable AI workloads to be deployed within days of hardware being installed. According to … continue reading
Kentik Launches Cause Analysis to Bring Network Expertise to Every Infrastructure Engineer
Kentik, the network intelligence platform, today launches Cause Analysis, a new AI-powered capability that automatically identifies and explains the cause of network traffic issues and anomalies which result in slow speeds, dropped connections, packet loss, and other service disruptions caused by factors like network congestion and hardware failures. Starting today, when sudden performance degradation, cost … continue reading
Komodor adds new cost optimizing capabilities to its Kubernetes management platform
Komodor is adding new cost optimization capabilities across its Kubernetes management platform so that organizations can reduce costs while still maintaining reliability across their Kubernetes environment. According to Komodor, IT teams often overspend on compute because right-sizing workloads can be difficult as a result of lack of expertise, the large volume of factors to consider, … continue reading
Pure Storage introduces Enterprise Data Cloud to enable centralized management of data and storage across on-premises, public cloud, and hybrid environments
Pure Storage is introducing a simpler approach to data and storage management that it says will allow organizations to focus more on business outcomes than on infrastructure. Enterprise Data Cloud (EDC) allows IT teams to centrally manage a virtualized cloud of data regardless of how many different locations it’s stored in, spanning on-premises, public cloud, … continue reading
VMware Cloud Foundation 9.0 delivers a “modern private cloud”
Broadcom has announced the release of VMware Cloud Foundation (VCF) 9.0, an update that it promises will provide “the agility and scalability of public cloud with the security, performance, architectural control and total cost of ownership (TCO) benefits of an on-premises environment.” It introduces a new unified interface for cloud administrators, including a new Quick … continue reading
Enterprise AI: A new game plan for storage IT professionals
As artificial intelligence (AI) becomes deeply embedded in enterprise operations, IT storage professionals are being pulled into uncharted territory. Where once their focus was confined to provisioning, performance tuning, data protection and backups, today they are expected to orchestrate data services, ensure regulatory compliance, optimize cost models, and even help train AI models. The transition … continue reading
Mirantis AI Factory Reference Architecture provides templates to support deployment and management of AI infrastructure at scale
Mirantis is introducing its AI Factory Reference Architecture, which provides blueprints for building and managing AI factories. Utilizing the company’s k0rdent AI platform that provides a templated, declarative model for rapid provisioning, the AI Factory Reference Architecture will enable AI workloads to be deployed within days of hardware being installed. According to Mirantis, cloud-native workloads … continue reading
Crack the Code: How Network Observability Unlocks Revenue Growth for Service Providers
Today’s service providers are operating in an era of relentless digital evolution, a time when standing still means falling behind. As they navigate a brutal battleground of cutthroat competition and sky-high customer demands, continued innovation is a must. To ensure their growth and very survival, managed service providers (MSPs), communication service providers (CSPs), and telecommunication … continue reading
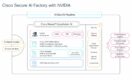
Cisco prepares for AI-ready data centers with new innovations, partnerships
During its annual conference, Cisco Live, Cisco announced several new offerings and partnerships that support its transition from traditional to AI-ready data centers. “Cisco is at the forefront of enabling organizations to harness the power of AI with solutions that are scalable, efficient, and, above all, secure. Our evolving portfolio lays the groundwork for AI-ready … continue reading
Contrast Security’s Northstar unifies app security for developers, security, and operations
Contrast Security has announced the launch of Northstar, a security platform update that brings developers, security, and operations teams together to address app security in a more unified way. “We’re calling this release Northstar because it points the way forward. It helps customers see what was once invisible — adding clarity where there was ambiguity, … continue reading
Opsera, Databricks expand partnership with DevOps for DataOps, Cloudera joins AI-RAN Alliance, and more: ITOps News Digest
AI-powered DevOps platform provider Opsera today announced the expansion of its Databricks partnership with the launch of its DevOps for DataOps capability, a Built on Databricks solution. Customers of Opsera and Databricks can use the solution to orchestrate end-to-end analytics and streamline delivery pipelines, the company wrote in its announcement. This is done through the … continue reading
Hope for Spring, Prepare for Frost: How to Think About AI’s Next Phase
Are we heading for another big freeze? ‘AI winter’ is a term that first emerged in the late 1970s, as disillusionment with contemporary AI projects came to a peak. Expectations were built up throughout previous decades with scientists and researchers expressing their intention to create machines that could think like humans. But eventually, the public … continue reading