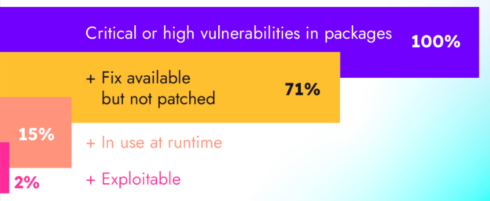
The need for more mature security practices when using cloud-native technology is clear with 87% of container images having high or critical vulnerabilities, up from 75% last year. Most of them at 71% of those vulnerabilities have a fix available that has not been applied.
This data comes from the new 2023 Cloud-Native Security & Usage Report published by monitoring tool provider Sysdig which gathered insights on cloud-native security and usage from a survey of over 1,250 IT professionals.
Another security issue is that 90% of granted permissions are not used, which leaves opportunities for attack.
“Despite increased adoption of shift-left security strategies to assess code early and often, organizations need runtime security. This is evidenced by the tremendous growth in the adoption of technologies like Falco, a Cloud Native Computing Foundation (CNCF) open-source project, that helps organizations detect runtime threats across clouds, containers, hosts, and Kubernetes environments,” the report states.
On a more positive note, however, only about 15% of those aforementioned high-level or critical vulnerabilities are being used at runtime, which is an opportunity to focus remediation efforts, according to the writers of the report.
Sysdig recommends organizations focus their remediation efforts on a smaller fraction of the fixable vulnerabilities that represent true risk by filtering on those vulnerable packages that are actually in use. This more actionable number can allay some fears around release decisions, provided organizations use the relevant security capabilities.
Increasing an organization’s security posture may be difficult now as companies are looking to tighten their budgets and their container usage has gone up. On top of that, over 72% of containers now have lifespans of fewer than five minutes, a higher percentage than in previous years, making it difficult to get accurate utilization and cost information about Kubernetes deployments, or rightsizing.