Topic: security
Microsoft launches Azure OpenAI Data Zones to give customers more flexibility over data residency
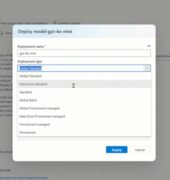
Microsoft has announced a new deployment option in Azure OpenAI that provides more flexibility and control over data privacy and residency for companies in the United States and European Union. With Azure OpenAI Data Zones, customers can process and store data within specific geographic areas without compromising performance. According to Microsoft, Data Zones allow for … continue reading
Edera releases open source container security benchmark and runtime scanner
Edera, provider of a secure-by-design Kubernetes and AI solution, today announced the availability of Am I Isolated, an open-source container security benchmark that probes users runtime environments and tests for container isolation. The Rust-based container runtime scanner runs as a container and detects gaps in users’ container runtime isolation. It also provides guidance to improve … continue reading
CrowdStrike to acquire Adaptive Shield
CrowdStrike has announced that it will be acquiring Adaptive Shield, a company that provides security monitoring capabilities for SaaS applications. “This acquisition will propel CrowdStrike to become the only cybersecurity vendor to provide full protection against identity-based attacks across the modern cloud ecosystem — from on-premises Active Directory to cloud-based identity providers and the growing … continue reading
Edera launches open source OpenPaX patch to improve memory safety in Linux
Container security company Edera is working to improve application-level memory safety in Linux with the release of OpenPaX, an open source kernel patch that mitigates common memory safety errors. It was initially created to benefit Edera’s own customers, but the company decided to open source it to make it available to the broader community. The … continue reading
Why your zero trust strategy will fail without automation
Zero trust is broken. Not because it’s a bad idea, but because most organizations are applying it wrong. If your security still depends on humans to approve access requests, verify identities, and respond to threats, you’re already behind. Zero trust’s core principle—trust no one, verify everything—breaks down when manual processes are too slow, error-prone, and … continue reading
Simbian’s new AI Agents enable more efficient security operations
The AI-powered IT security company Simbian has announced a set of three new AI Agents that can “work alongside security teams to enhance the intelligence, speed, and coverage of their entire security program.” SOC Agent investigates and responds to security alerts, leveraging knowledge from security experts, the company’s playbooks, and user guidance to create responses … continue reading
Having a Cyber Resiliency plan – and Cleanroom Recovery – is critical to restoring systems after malicious attacks
In today’s threat landscape, a single ransomware attack can cripple a business for weeks, underscoring the critical importance of cyber resiliency. Attacks are becoming more common and more sophisticated, leaving businesses struggling with staggering costs and devastating downtime. Here’s a concerning reality: many organizations currently believe their recovery strategies will protect them in the event … continue reading
Podcast: Diving into NIST’s quantum-safe algorithms
There’s been a concern that quantum computers could break the current encryption algorithms we use to protect data today. Recently, NIST announced the approval of three quantum-safe algorithms that could withstand quantum computers. IBM developed two of the approved algorithms, so on the most recent episode of our podcast, Get With IT, we interviewed Vadim … continue reading
Stytch updates Device Fingerprinting to improve bot detection
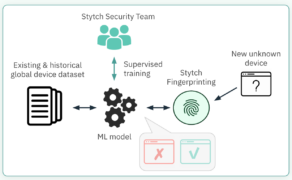
The authentication provider Stytch is releasing new features in its Device Fingerprinting offering aimed at making it easier for companies to detect bots and fraud. Stytch Device Fingerprinting creates unique and persistent fingerprints for each visitor by analyzing subsignals of device hardware, network TLS profile, and active browser markers. It is also invisible to users, … continue reading
Report: AI may have benefits across enterprise, but it’s causing trouble for IT
A majority of IT leaders are worried about the cybersecurity implications brought on by the introduction of AI into their organizations. According to Flexential’s 2024 State of AI Infrastructure Report, 95% of IT leaders said that AI has made their organization more vulnerable to cyberthreats. About half of the respondents believe this is because the … continue reading
Docker will soon deprecate password logins via CLI when SSO enforcement is on
Starting September 16th, Docker is deprecating the ability to use passwords to sign-in to services via its CLI when users have Single Sign-On (SSO) enforcement turned on. SSO enables users to authenticate once and get access to multiple different services. In this case, that includes Docker Desktop, Docker Hub, Docker Scout, and Docker Build Cloud. … continue reading
Fortanix adds File System Encryption in latest release
The security company Fortanix has announced File System Encryption, a new feature that is part of the Fortanix Data Security Manager. With File System Encryption, data can be encrypted at the file system level, which is useful in scenarios where different user groups need access to different parts of a database. Organizations can set up … continue reading