Topic: authorization
Cerbos Hub launches to simplify deployment of authorization policies
The authorization company Cerbos has announced the general availability of Cerbos Hub, which is a management system for authoring, testing, and deploying authorization policies using the company’s open-source authorization layer Policy Decision Point (PDP). With PDP, authorization policies are separated from application code, which allows authorization to scale and change as the application’s needs change … continue reading
ITOps Times Open-Source Project of the Week: Keycloak
With Keycloak, users can add authentication to applications and secure devices with minimum effort. The project provides user federation, strong authentication, user management, fine-grained authorization, and more. Keycloak provides single-sign out, which means users only have to log out once to be logged out of all applications that use Keycloak. By configuring the Identity Provider … continue reading
Styra introduces new authorization policy tools
The creators and maintainers of Open Policy Agent (OPA), Styra, announced a broad policy library and toolset for infrastructure for Styra Declarative Authorization Service (DAS). Styra now offers hundreds of validated policies from its expanded library that are compliant with NIST Special Publication (SP) 800-190, in order to address security concerns related to the use … continue reading
ITOps Times Open-Source Project of the Week: Red-Shadow
Cloud security provider Lightspin developed a new open-source scanner Red-Shadow that reports when user permissions are loosely defined, which opens up an attack path for hackers. Lightspin released the scanner after it announced the results of its research that discovered a gap between AWS Identity and Access Management (IAM) user group policies that attackers can … continue reading
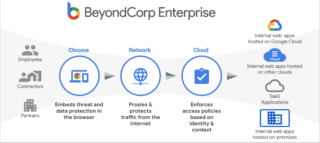
Google announces BeyondCorp Enterprise, its new zero trust product offering
Google announced the release of BeyondCorp Enterprise which extends and replaces BeyondCorp Remote Access for companies to start their own zero-trust implementation. The solution includes non-disruptive, agentless support through the Chrome Browser, access to Google’s global network, and the entire surface area is protected by Google’s scalable DDoS protection service, which has been proven to … continue reading