Tigera has announced several updates to its open source container networking and security tool, Project Calico.
The Calico Ingress Gateway now includes WAF capabilities for inspecting, authorizing, and securing ingress traffic at runtime. Users will be able to define and enforce security policies at the ingress gateway, which allows for deeper inspection of HTTP and gRPC traffic and enables more proactive blocking of threats.
“Using a WAF that is integrated with Calico Ingress Gateway supports a defense-in-depth approach by adding another layer of protection at the cluster boundary,” Tigera wrote in a blog post.
Additionally, support was added for centralized log forwarding for VM and bare metal hosts not running in Kubernetes. Logs are collected at a central point, like a management cluster, and then are forwarded to an external log store. According to the company, this reduces operational overhead, minimizes the risk of misconfigurations, and makes it easier to maintain consistent logging.
Calico Dashboards also now feature improved Role-Based Access Control (RBAC) for accessing observability data, so that companies can ensure that developers are only able to access data related to their applications. Additionally, UI improvements were added to the dashboard, including clearer card labels and control over which columns are displayed.
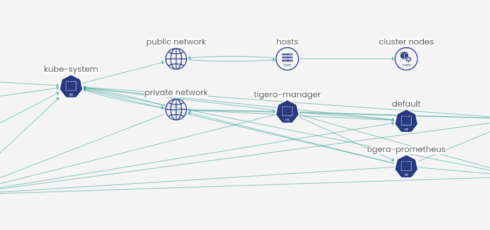
The iconography in Calico Service Graph was also updated to make it easier to distinguish between Kubernetes cluster nodes and standalone VM and bare metal hosts.
“Many of our customers are increasingly using a mixture of workload types, including both VMs and containers. Customers often choose to keep their databases running on VMs because they are highly performance-tuned. And when troubleshooting, it is incredibly helpful for these customers to easily and visually identify each workload type (VM/container/bare metal) and see the traffic flowing between them,” Tigera wrote.
Finally, Calico Cloud Free Tier users can now take advantage of automatically generated network policy recommendations based on their flow logs. The free tier only utilizes 24 hours of log data to generate recommendations, compared to 7 days for commercial versions, and also only generates rules that specify IP addresses, whereas the commercial version can generate DNS rules for egress traffic.
“As organizations scale their Kubernetes environments, many struggle to ensure security due to the siloed, disparate solutions used for Kubernetes security,” said Phil DiCorpo, senior director of product management at Tigera. “Calico’s new capabilities are a testament to our ongoing commitment to delivering a single, comprehensive platform that enables security across every aspect of the customer’s Kubernetes journey.”








