When server infrastructure underwent its transformation with the rise of containers and Kubernetes, it wasn’t just a technical shift — it was a shift in mindset. Static workloads maintained like fragile pets were replaced by disposable, declarative, policy-managed containers orchestrated at scale. Now, the same change is coming for the networking layer.
For years, network teams have tried to match the speed and automation of platform teams. Many have adopted scripts, APIs, and infrastructure-as-code tools. Yet in practice, most enterprises still rely on tickets: someone requests a change, someone else approves it, and days or weeks later the network finally adjusts. Even with backend automation, without true self-service at the front end, this manual bottleneck remains. And modern applications expect more.
Today’s distributed systems and AI-driven workloads assume the network is as dynamic and programmable as compute. Meeting this expectation means moving away from manually approved changes toward a model where networking is declarative, versioned, and deployed through the same automated workflows as the applications it connects. In other words: from TicketOps to GitOps.
A Kubernetes-Native Network for Any Environment
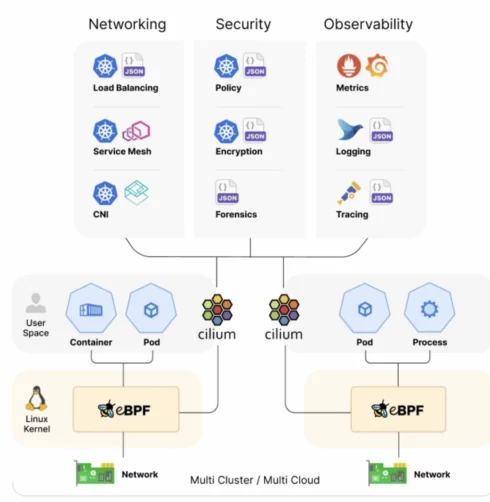
Just as Kubernetes abstracts server complexity, modern network programmability removes hardware dependencies and vendor silos. Emerging technologies make it possible to apply the same security and connectivity policies across containers, virtual machines, and legacy workloads.
This lets teams define security intent once and enforce it consistently across Kubernetes clusters, virtual machines, and even bare metal servers — without managing separate tools or duplicating work. This alignment cuts friction and helps operations teams treat the network as a flexible extension of the application platform.
Unifying Kernel, Network, and Namespace
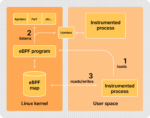
The foundation for this flexibility is the ability to program the network directly inside the operating system kernel. Technologies like eBPF run networking tasks such as routing, filtering, and packet inspection right where traffic originates. This deep visibility supports real-time policy enforcement, detailed telemetry, and adaptive routing.
Traditional network security relied on static IP addresses and perimeter firewalls. In a dynamic environment, IPs shift constantly and make poor security markers. Modern identity-aware policies use workload metadata to control access and adapt automatically as applications scale or move.
This approach now extends beyond Linux. Programmable security and observability are reaching Windows Server workloads too, closing a major visibility gap in many enterprises. Programmable pipelines also help control observability costs by filtering out low-value telemetry before it hits expensive analytics systems.
Plus, this same programmable foundation allows teams to apply critical security patches live, without taking servers or network devices offline — shrinking maintenance windows and reducing risk.
Moving from TicketOps to GitOps
In the traditional model, network changes still flow through ticket queues. Users submit requests, compliance checks happen, and an engineer eventually implements the change. This delays deployments and invites human error.
GitOps replaces this by managing network policies as code. Changes are version-controlled, peer-reviewed, and automatically deployed through CI/CD pipelines alongside application updates.
The real breakthrough comes with true self-service. For example, a developer launching a new microservice can automatically provision secure east-west connectivity, encryption rules, and flexible layer 3–7 load balancing — even when workloads span Kubernetes clusters and virtual machines. No manual tickets required.
Network and Platform Teams: Better Together
As programmable networking matures, traditional network engineering and platform engineering are blending. Platform teams excel at building self-service portals and pipelines but often need deeper expertise in routing, segmentation, and compliance. Network engineers bring this know-how but must adopt cloud-native workflows and tools.
Modern programmable networks bridge this gap. Platform engineers embed security and connectivity directly in their automation, while network engineers maintain visibility, enforce zero-trust boundaries, and troubleshoot with the same shared tooling. This ensures applications deploy faster and stay secure.
Conclusion: The Network as a Core ITOps Building Block
The same transformation that reshaped servers is now changing networks. Stability and security are still vital, but programmability, real-time observability, and developer-friendly workflows are just as important.
Moving from TicketOps to GitOps turns networking into a versioned, declarative, and automated layer that scales with modern workloads. It aligns network operations with how teams already build and ship software, cutting delays and boosting reliability.
The network is no longer just a passive dependency or a backlog of tickets. It is a core ITOps building block — programmable, secure, and integrated by design.