Topic: vulnerabilities
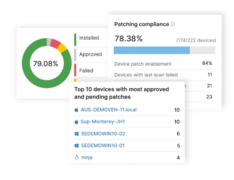
NinjaOne adds new capabilities for unifying vulnerability management and patching
NinjaOne, a company that provides endpoint management solutions, today announced new features that will make it easier for IT teams to deal with vulnerabilities and manage patches. It will now provide a single platform from which IT teams can identify, assess, prioritize, and patch vulnerabilities. The solution can also automatically detect and deploy patches across … continue reading
Patch management can be a challenge, but not impossible
Updating systems on a regular basis is one of the best lines of defense against cyberattacks, but many companies are still struggling to effectively do patch management. According to a study conducted by ServiceNow and the Ponemon Institute, of the nearly half of respondents who had a data breach in the past two years, 60% … continue reading
Researchers find vulnerability in popular Bluetooth-enabled devices
Internet-connected devices are opening up a wide range of applications from mobile devices to home appliances and wearables, but these devices are also opening up new areas of attack. Researchers from Boston University found that a third-party algorithm can track the location of some Bluetooth devices such as Fitbits, smart pens and even Windows and … continue reading
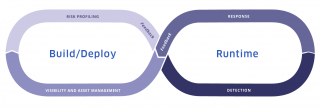
StackRox Container Security Platform expands its scope to the orchestration level
Containerized and cloud-native application security company StackRox announced the latest release of its Container Security Platform today. The updated platform aims to provide an all-in-one solution for securing containers through runtime threat detection as well as actionable feedback at every stage of the container lifecycle. “The StackRox Container Security Platform’s integrated approach streamlines decision making … continue reading