premium AIOps: A Self-Healing Mentality
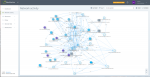
The first time I watched Minority Report back in 2002, the film’s premise made me optimistic: Crime could be prevented with the help of Precogs, a trio of mutant psychics capable of seeing crimes before they happen, enabling police to stop murderers before they act. What a great utopia! I quickly realized, however, that this “utopia” … continue reading
Sensu announces the general availability of Sensu Go, the latest cloud-native monitoring software for enterprises
Sensu, Inc., a leader in open source monitoring, today announced the general availability of Sensu Go, a scalable, powerful and user-centric monitoring event pipeline, designed to improve visibility and streamline workflows for enterprises. Sensu empowers businesses to gain deep visibility into their infrastructure, from Kubernetes to bare metal, providing a single source of truth among application … continue reading
Splice Machine closes $16 million Series B funding round
Splice Machine, the leading data platform for operational artificial intelligence (AI), today announced it has closed $16 million in additional funding led by GreatPoint Ventures (GPV). Accenture Ventures also joined this round, strengthening the partnership between Accenture and Splice Machine to drive mission-critical business outcomes for global clients with operational AI solutions. Also participating in the round is Allen Miner, CEO of the … continue reading
Tenable announces new insights into risks across IT/OT environments
Cyber exposure company Tenable has announced a new integrated Cyber Exposure solution, which combines Tenable Industrial Security and Tenable.sc. According to the company, the solution offers a unified view of cyber risk across IT and operational technology (OT) networks. The integration will enable security professionals to measure, manage, and reduce cyber risk from a single … continue reading
“Doomsday” flaw discovered in RunC underscores potential for critical container vulnerabilities
The discovery of a major security flaw in the common open-source runtime engine for Docker, Kubernetes and other container management systems, points to an underlying risk associated with containerized applications. Researchers Adam Iwaniuk and Borys Popławsk discovered the vulnerability, CVE-2019-5736, in RunC, the common runtime engine developed by Docker and now a common Open Container … continue reading
How to keep costs down in the cloud
There are many reasons companies are growing their investments in the public cloud, from needing to innovate faster and deliver better service to customers or to support DevOps workflows and modern applications. Yet cost savings is still a driving incentive for many CIOs. The metrics are undeniable: reports vary from an automatic savings of 10 … continue reading
NeuVector to offer service mesh protection
Container network security provider NeuVector is giving users a new layer of security for service meshes. The company announced integration for the service meshes Istio and Linkerd, designed to expand security capabilities to production Kubernetes deployments. The new integration was developed in collaboration with IBM Cloud and the Istio open-source development team. According to the … continue reading
SnapRoute delivers cloud-native network operating system
Saying that today’s network operating systems are keeping organizations from fully taking advantage of modern software architectures, SnapRoute today announced it is making available its Cloud Native Network Operating System (CN-NOS). The CN-NOS is containerized and cloud-native, and uses DevOps principles to give organizations the ability to deliver new services more rapidly and reliably as … continue reading
IoT is driving organizations to the edge
The surge in the number of connected devices has created an immersive and collaborative interface between people and things, which is driving the need for new models of compute and infrastructure. Traditional centralized, mega-scale cloud data centers, augmented by distributed content delivery networks (CDNs), do not adequately meet the performance needs demanded by this explosion … continue reading
Red Hat deepens integration with Ansible Automation in Cloudforms 4.7
Red Hat has announced the latest version of the Cloudforms infrastructure management tool. Red Hat Cloudforms 4.7 introduces further integration with Ansible Automation and new integrations to streamline and simplify IT management in hybrid cloud infrastructures. The enhanced integration with Ansible introduces new Ansible capabilities to Cloudforms, such as the ability to execute Ansible Tower … continue reading
Rancher Labs supports multi-cluster Kubernetes applications
Rancher Labs today announced support in its open-source management platform for multi-cluster global Kubernetes applications, which the company believes will be a big reason for that platform’s uptake going forward. “The number of production clusters is showing that multi-cluster with Kubernetes is becoming a reality,” said Sheng Liang, co-founder and CEO of Rancher Labs. “Everything … continue reading
Citus brings coveted extensions to Microsoft’s Azure database PostgreSQL service
While Microsoft’s recent acquisition of PostgreSQL database provider Citus Data moves the company deeper into the open source world, it addresses a far greater need to bring more scale to the Azure database-as-a-service portfolio. Microsoft’s focus on open source across the board is no longer in dispute. It’s now safe to say that Microsoft has … continue reading
Platform9 launches managed Kubernetes service on VMware
Hybrid cloud provider Platform9 has announced a new managed Kubernetes service on VMware vSphere. According to the company, Platform9 Managed Kubernetes (PMK) will reduce the operational complexity of Kubernetes and provide out-of-the-box enterprise-grade capabilities, such as zero-touch upgrades, multi-cluster operations, high availability, and monitoring. PMK will allow organizations to modernize their VMware environments while also … continue reading
When business services fail due to IT cyberattacks & how to protect your organization
When we think about cybersecurity, we most often think about compromised PII — Personally Identifiable Information. PII includes the social security numbers, account numbers, addresses and so on that allow bad actors to open unauthorized accounts in people’s names, to drain existing accounts, and to generally create adverse and hard-to-reverse impacts on the victims. Generating … continue reading